The telegraph had gradually come into use in the two decades before the civil war. The North being far more industrialized than the South and accordingly had an more extensive telegraph network than the South. Consequently, the South had simple needs and used a variety of substitution ciphers of the type we are all familiar with. The North is another matter, it used what is called a route cipher and it stayed unbroken through out the war. That isn’t say that code books and operators weren’t captured through out the war but this necessitated changing the code books not changing the cipher method. There really isn’t a single Northern code as such, the code started out simple and as the war progressed the code was revised from time as code books or operators were captured or otherwise compromised. Additionally, there wasn’t just one code in use at any one time, there could be any number of codes in use as each telegraph pair could decide on which code they might use on any day. Additionally, the use of paper and pencil decoding methods made decoding too time consuming to be of any practical use.
Routing Cipher
Suppose you wanted to send the message “Attack at dawn six thirty am” using civil war routing techniques, you would first choose a square matrix slightly larger than the message. In this case you might select one called “eagle” which in our imaginary code book is a 5X5 matrix which is two characters larger than our message. We would write our message in capital letter in the matrix starting with the top left position and continuing line by line until the message is all spelled out. Fill in each unused space with an “X” or whatever letter you’ve agreed to use for dummy characters.
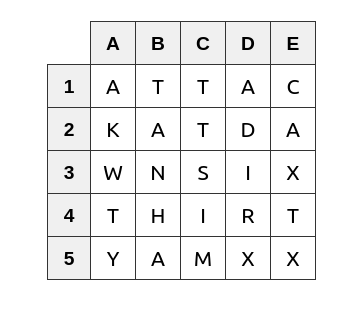
The next step is what made the routing cipher so hard to break with paper and pencil methods. Code “eagle” then had the sender rewrite the matrix by copying each column into a row with a predetermined sequence which we will say is B to 1, C to 2, A to 3, E to 4 and D to 5. This gives us a rearranged unreadable matrix
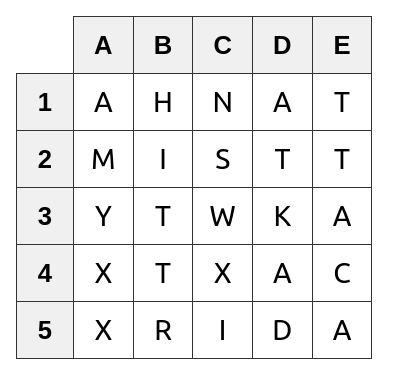
The encoded message would be transmitted as a Morse code string as “EAGLEAHNATMISTTTYWKAXTXACXRIDA”. Messages were always preceded by the code key. The person receiving the encoded message would look up “eagle” in his code book to determine the decoding sequence. The decoding sequence would be to copy 1 to B, 2 to C, 3 to A, 4 to E, and 5 to D. This would restore the message. Any spy listening could eventually decrypt the message but this probably take far longer to be of any use on the battle field.
ChatGPT program used to draw the 5 x 5 grid.
I asked ChatGPT to create a Python3 program to draw a 5 X 5 grid which it did in a few seconds. After downloading the code to my desktop, I ran it and the 5 X 5 grid appeared as desired. Because things were interactive, the two illustrations were created, screen shots were taken, resized, and saved as .PNG files. The two illustration .PNG were then uploaded to WordPress and you see the results above.
I can’t tell you how many computer languages this version of ChatGPT can generate code for but it created a JavaScript, PHP version of a 26 X 26 grid to run on my server.
The link below discusses ChatGPT from a programmer’s perspective.